Introduction
In a digital landscape plagued by sophisticated cyber threats, traditional perimeter-based security models are no longer sufficient. Organizations of all sizes are adopting Zero Trust Security as a proactive defense strategy. Rooted in the principle of “never trust, always verify,” this model enforces strict identity verification and access control for all users and devices, regardless of their location on or off the network.
What Is Zero Trust Security?
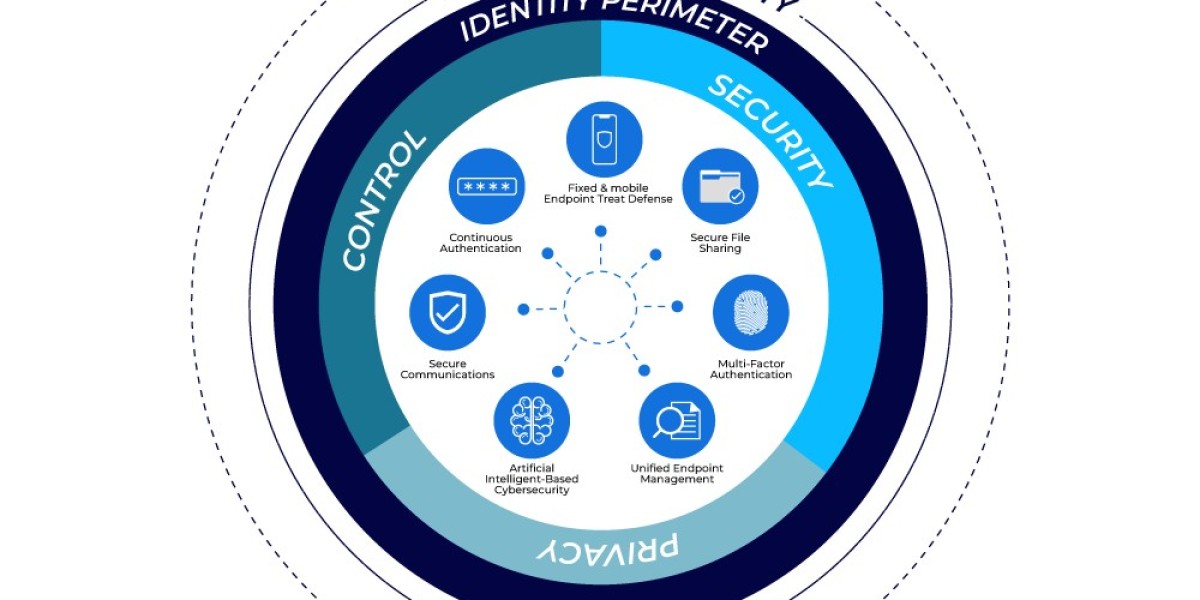
Zero Trust Security is a cybersecurity framework that requires every user, device, and application to be continuously authenticated, authorized, and validated before gaining access to data or services. Unlike traditional models that assume trust within the internal network, Zero Trust treats all traffic as untrusted until proven otherwise.
Key Principles of Zero Trust Security
- Verify Explicitly
Access decisions are based on multiple data points, such as user identity, device health, location, and behavior patterns. Authentication is continuous, not one-time. - Least Privilege Access
Users are granted the minimum access necessary to perform their tasks. This reduces the risk of insider threats and limits the potential impact of compromised accounts. - Assume Breach
Zero Trust operates under the assumption that a breach has either already occurred or is imminent. Continuous monitoring, threat detection, and rapid response are critical components. - Micro-Segmentation
The network is segmented into smaller zones, making it difficult for attackers to move laterally within a compromised environment. Each segment enforces its own access rules. - Multi-Factor Authentication (MFA)
MFA is a cornerstone of Zero Trust, requiring users to prove their identity through multiple factors like passwords, biometrics, or hardware tokens.
Benefits of Zero Trust Security
- Enhanced Data Protection
By validating every access request, sensitive data is better shielded from unauthorized access, reducing data breach risks. - Improved Compliance
Zero Trust helps organizations meet regulatory requirements such as GDPR, HIPAA, and PCI-DSS by enforcing stringent access and audit controls. - Reduced Attack Surface
Limiting user and device access only to necessary resources minimizes the areas available for exploitation by malicious actors. - Adaptive Security Posture
Zero Trust dynamically adjusts access permissions based on real-time risk analysis, ensuring more responsive and resilient defense.
Common Implementation Components
- Identity and Access Management (IAM):
Centralized user identity systems that ensure access policies are uniformly enforced. - Endpoint Detection and Response (EDR):
Security tools that continuously monitor and respond to threats on endpoint devices. - Security Information and Event Management (SIEM):
Platforms that aggregate and analyze logs to detect suspicious behavior across the environment. - Zero Trust Network Access (ZTNA):
A modern alternative to VPNs, ZTNA allows secure remote access to specific applications rather than entire networks.
Challenges in Adopting Zero Trust
- Cultural Resistance:
Transitioning to Zero Trust requires a shift in mindset from traditional trust-based models, which may face internal resistance. - Complexity in Integration:
Organizations with legacy systems may encounter difficulties when integrating Zero Trust solutions with existing infrastructure. - Cost and Resources:
Initial investment in tools, training, and personnel can be significant, especially for small to mid-sized enterprises.
Best Practices for a Successful Zero Trust Strategy
- Start with High-Risk Assets:
Identify critical data and applications and implement Zero Trust controls around them first. - Establish Clear Policies:
Define who should have access to what, when, and under what circumstances. Use role-based access controls to streamline this process. - Use Automation:
Automated policy enforcement and monitoring reduce the risk of human error and speed up threat response. - Regularly Review Access Rights:
Conduct periodic audits to ensure users have only the permissions they need and revoke access that’s no longer required. - Educate Employees:
Training staff on Zero Trust principles fosters a security-first culture and reduces the likelihood of unintentional breaches.
Source - https://www.marketresearchfuture.com/reports/zero-trust-security-market-8642
Zero Trust Security is more than a buzzword—it’s a strategic framework essential for navigating today’s complex cybersecurity environment. By discarding implicit trust and enforcing continuous verification, organizations can significantly enhance their security posture. While implementation can be complex, the long-term benefits of greater control, visibility, and resilience make Zero Trust an investment worth making.